Ransomware viruses come in many forms, but they all have one thing in common: They're all designed to encrypt your files, present you with a ransom note, and force you to pay money to get your digital files back.
Sometimes the ransom note simply appears on your screen. Other times it takes over your wallpaper, replacing it with instructions on how to begin the process of paying the ransom. But whatever method, you can bet that it's a jarring and unsettling experience. The good news is that, if you have a high-quality cloud backup system in place, you can get your data back without paying the ransom.
Here are a few examples of ransom notes you might see if your computer becomes infected with ransomware.
1. Cerber reads the ransom note for you
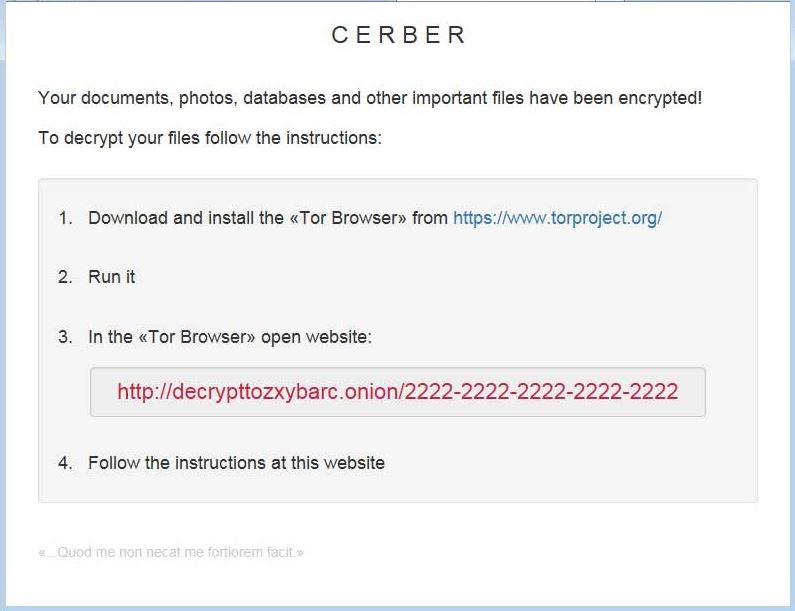
Sometimes referred to as "The Talking Ransomware," Cerber ransomware famously uses text-to-speech technology to read its ransom note to victims. Cerber attacks have been on the rise since last April. Cybercriminals began spreading the malicious software using the same spam email infrastructure used to distribute the successful Dridex virus which started making the rounds last fall. Variants of Cerber have also surfaced, including one that can launch DDoS attacks.
Interestingly, if you look at the bottom of the Cerber ransom note, you'll find the Latin quote "Quod me non necat me fortiorem facit," which in English means, "That which does not kill me makes me stronger." I'm sure that makes Cerber victims feel better.
2. CryptoWall remains a major threat
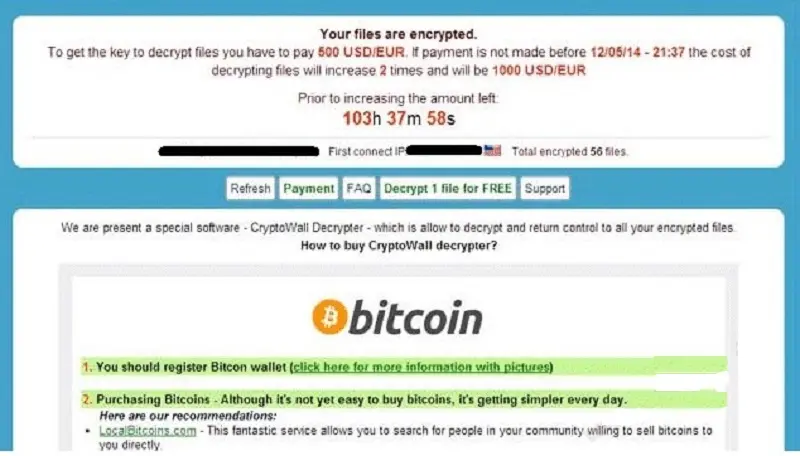
One of the most famous names in ransomware, CryptoWall and its variants consistently rank among the top five cybersecurity threats, according to statistics compiled by IT security firm Fortinet.
This CryptoWall ransom note was provided by Diverse Technology Solutions (DTS), a Carbonite Partner based in Tiffin, Ohio. DTS successfully used Carbonite to restore a healthcare facility's data following a CryptoWall attack. Thanks to Carbonite cloud backup, the healthcare facility was able to get its data back without paying the ransom. The key to recovering from ransomware without having to pay off cybercriminals is to be proactive and invest in backup before you're attacked.
3. Locky makes big headlines in 2016
Locky has consistently ranked among the top cybersecurity threats – at least it was until one month ago. Over the last few weeks, researchers have seen a steep decline in new Locky ransomware infections. Researchers note, however, that the battle is not over yet. Individuals and businesses need to remain vigilant.
Locky first achieved notoriety in February after infecting IT systems at Hollywood Presbyterian Medical Center in Los Angeles. The attack forced hospital staff to declare an internal state of emergency and several patients had to be transported to other facilities to receive care. The hospital regained access to its systems after paying a $17,000 ransom.
Locky is most often spread via macros found in Microsoft Word. Victims typically receives an email with a Microsoft Word document attached to it. Upon opening the document, the victim is asked to enable macros. When the victim enables macros, the malware begins to encrypt the files on the victim's computer. The virus also attempts looks for network connections in an effort to spread itself further.
Once a victim's computer is taken over by Locky, their wallpaper will be replaced with a message similar to the one above.
Want to learn more? Read these tips on how to avoid or defeat a ransomware infection today.
Ready to protect your computers from ransomware? Learn more about Carbonite backup solutions today.










